最近在浏览器(Chrome 85.0.4183.121)调试网页的时候,出现如下警告信息:
|
|
Indicate whether to send a cookie in a cross-site request by specifying its SameSite attribute Because a cookie's SameSite attribute was not set or is invalid, it defaults to SameSite=Lax, which prevents the cookie from being sent in a cross-site request. This behavior protects user data from accidentally leaking to third parties and cross-site request forgery. Resolve this issue by updating the attributes of the cookie: Specify SameSite=None and Secure if the cookie should be sent in cross-site requests. This enables third-party use. Specify SameSite=Strict or SameSite=Lax if the cookie should not be sent in cross-site requests 22 cookies 3 requests Learn more: SameSite cookies explained |
具体如下图:

这个问题的原因是为了解决跨站请求伪造(CSRF),需要服务器设置Cookie策略。
对于ubuntu 16.04/apache 2.4上执行如下配置:
|
|
# 启用 headers 模块 $ sudo a2enmod headers $ sudo service apache2 restart # 观察是否启用成功 $ sudo apachectl -M | grep headers |
编辑网站的访问控制配置文件.htaccess,配置策略:
|
|
#跨站请求伪造CSRF防御,严格设置Cookie策略,不允许Cookie的非同源传递 <IfModule mod_headers.c> #Always add cookie policy Header always set Set-Cookie "HttpOnly; Secure; SameSite=Strict" #Strip off double Secure or HttpOnly settings as if App and Apache sets above you can sometimes get both Header always edit Set-Cookie ^(.*);\s?Secure;?\s?(.*);\s?Secure;?\s?(.*)$ "$1; $2; $3; Secure" Header always edit Set-Cookie ^(.*);\s?HttpOnly;?\s?(.*);\s?HttpOnly;?\s?(.*)$ "$1; $2; $3; HttpOnly" #Strip off double ;; settings Header always edit Set-Cookie ^(.*);\s?;\s?(.*)$ "$1; $2" </IfModule> |
生效之后,在服务器的响应报文的报文头中会出现箭头指示的信息,代表配置成功。
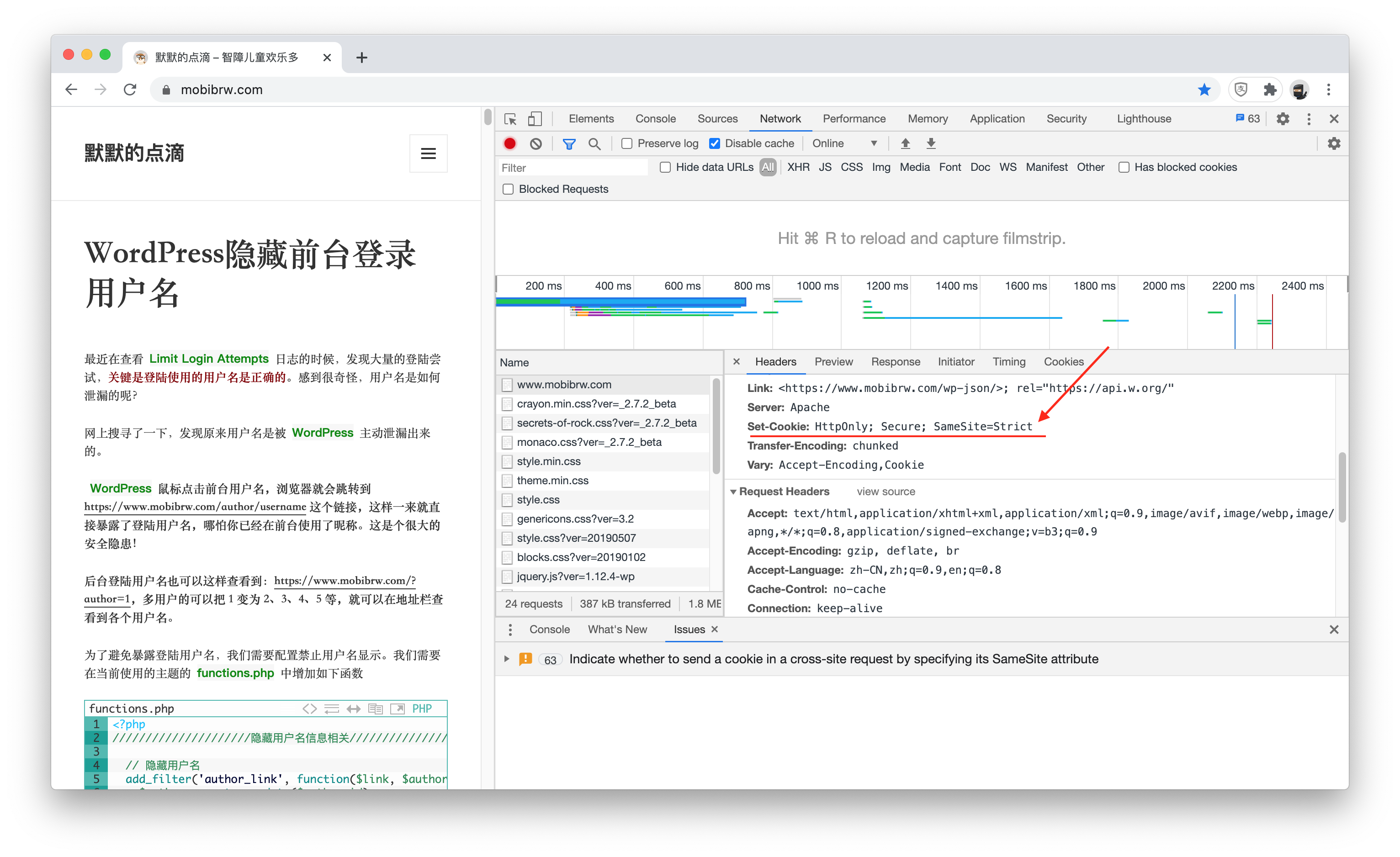
目前发现设置之后,Wordpress无法正常登陆,编译文章的时候,总是提示本地文件跟服务器上的不匹配,看来是浏览器跟服务器之间的兼容性还存在问题,因此暂时不开启这个功能吧。
参考链接

